4 Ways Ransomware Companies Behave Like Legitimate BusinessesThe nefarious firms that target your data have become pretty sophisticated operations.
ByLiz Webber•
Ransomware -- applications that encrypt all the data on a computer then demand payment to unlock it -- have become a pervasive threat to businesses.
Last Friday'sWannaCry attackwas unusual in its scope, with reports that 10,000 organizations were hit in 150 countries, but business owners are no stranger to ransomware. Close to half of U.S. companies have beenvictims of ransomware attacks, according to a 2016 report from Osterman Research.
While the sums demanded are generally low, the costs have been going up. Symantec reports that theaverage ransom was $679 in 2016, up from $294 in 2015. The FBI estimated ransomware firms wouldcollect $1 billionin 2016.
And that's just the attacks that are reported. Because the ransom amounts are often less than what would be covered by insurance, and no data is actually compromised, many victims keep it to themselves. Less than one in four attacks are据报道,当局, according to Datto, a company that helps companies back up and recover their data.
Datto has seen first-hand the rise of ransomware incidents.
"At first it was an anomaly. And then over time ended up being something that really just started to affect our partners almost en masse," CEO Austin McChord says.
About a year ago, Datto decided to make data recovery a bigger part of its business. The company established a dedicated team called Code Red and built a lab to infect its own computers with ransomware to see how it worked. What Datto found is that the companies that use ransomware have adopted some pretty sophisticated business practices.
Here are a few ways ransomware companies act like legitimate businesses:
1. Ransomware has built-in A/B testing to find the optimal ransom amount.
One of the first things that Datto noticed was that the programs asked for varying ransom amounts.
"If we put different amounts of data or different types of data, we can see that the ransom numbers would be different, like what it was actually charging for ransom," McChord says. He adds that he believes the perpetrators of ransomware attacks track which of the computer-generated amounts victims are most likely to pay and use that data to adjust their demands.
2. Attackers research targets extensively to find an opening.
Much like marketers researching a target client, ransomware companies take time to crawl employees' public digital presence in order to send personalized emails that appear to come from a family member, friend or business associate. That false connection tricks the unsuspecting employee into downloading the ransomware.
3. Some ransomware includes friendly tech support.
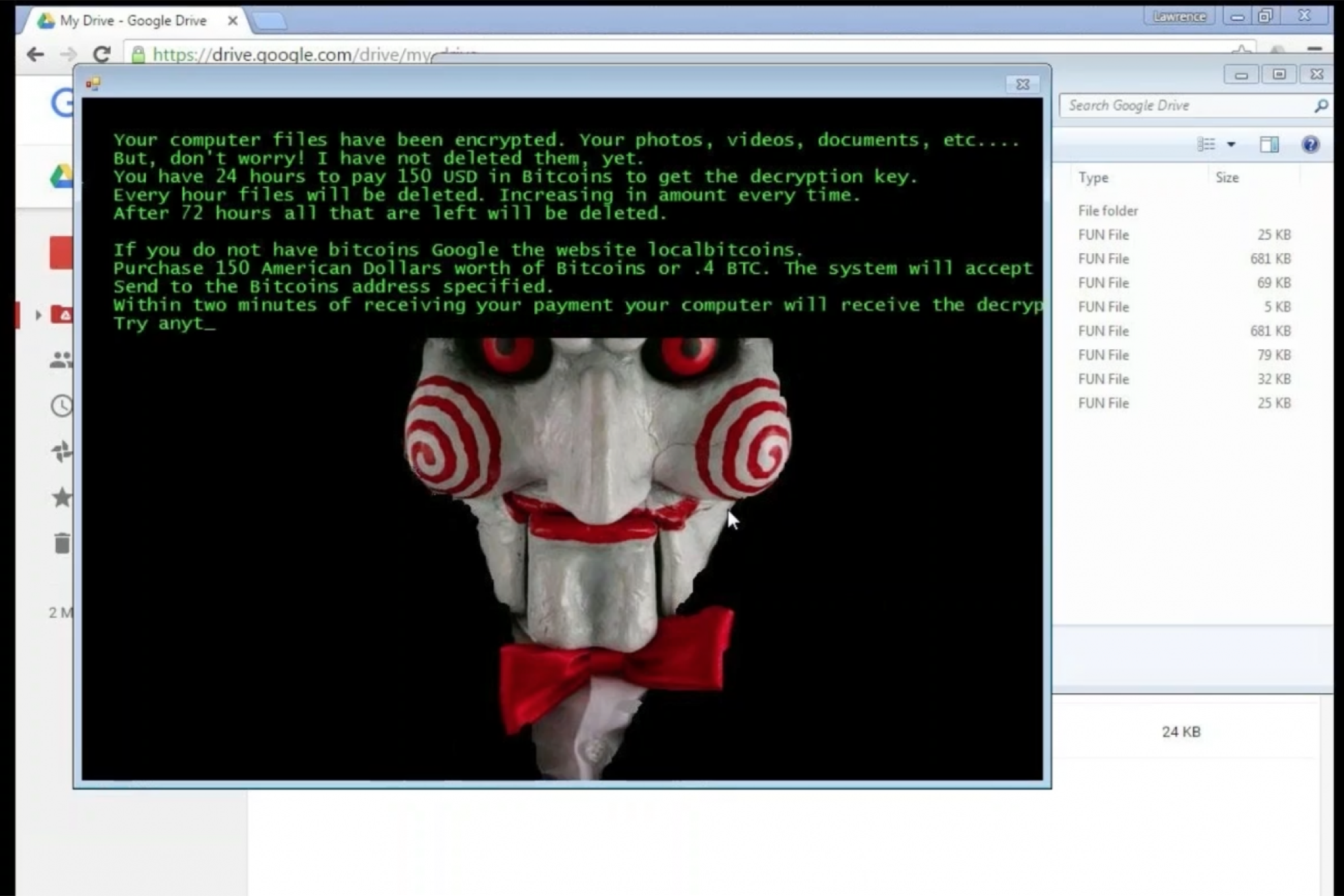
Many ransomware victims are understandably unsure how to proceed when their data is encrypted, particularly when it comes to steps such as obtaining the Bitcoin the attackers demand as payment. In an ironic twist, some programs are more than happy to offer tech support via "helpful" pop-up messages.
"It's almost interesting the sort of the language that they [use to] talk about it, as though this program that is the actual ransomware application is there to help you. "Let's help you get your files back. Here are the steps you need to take,'" McChord says.
Other software takes a more sinister approach. One program Datto investigated (pictured above) used the clown character from the Saw film franchise and threatened to delete a file for every hour that the ransom went unpaid.
4. Ransomware won't attack you right away.
一旦邪恶的应用程序下载,它often lurks in the background for a few days so that victims forget they downloaded it.
"The fact that the ransomware lies in wait for a while is not that dissimilar to a drip campaign in marketing," McChord says. "You'll sign up for something and then it might be a while before you actually start getting those emails."
How can businesses avoid a ransomware attack?
While up-to-date cybersecurity software is important, keeping your business safe comes down to educating employees on avoiding questionable downloads.
"Lots of people think that because they have this firewall or because they have this [antivirus] software they're safe and they're covered," McChord says. "But when you open that app and you get that box that comes up in Windows that says "so and so wants to modify buh buh buh on your computer' and you say "OK,' you just dismissed all of that protection."
Ultimately, the way to stop ransomware for good may be for more companies to back up their data so it can be easily recovered after an attack. If victims stop paying the ransoms, the attacks will no longer be a viable business strategy.












